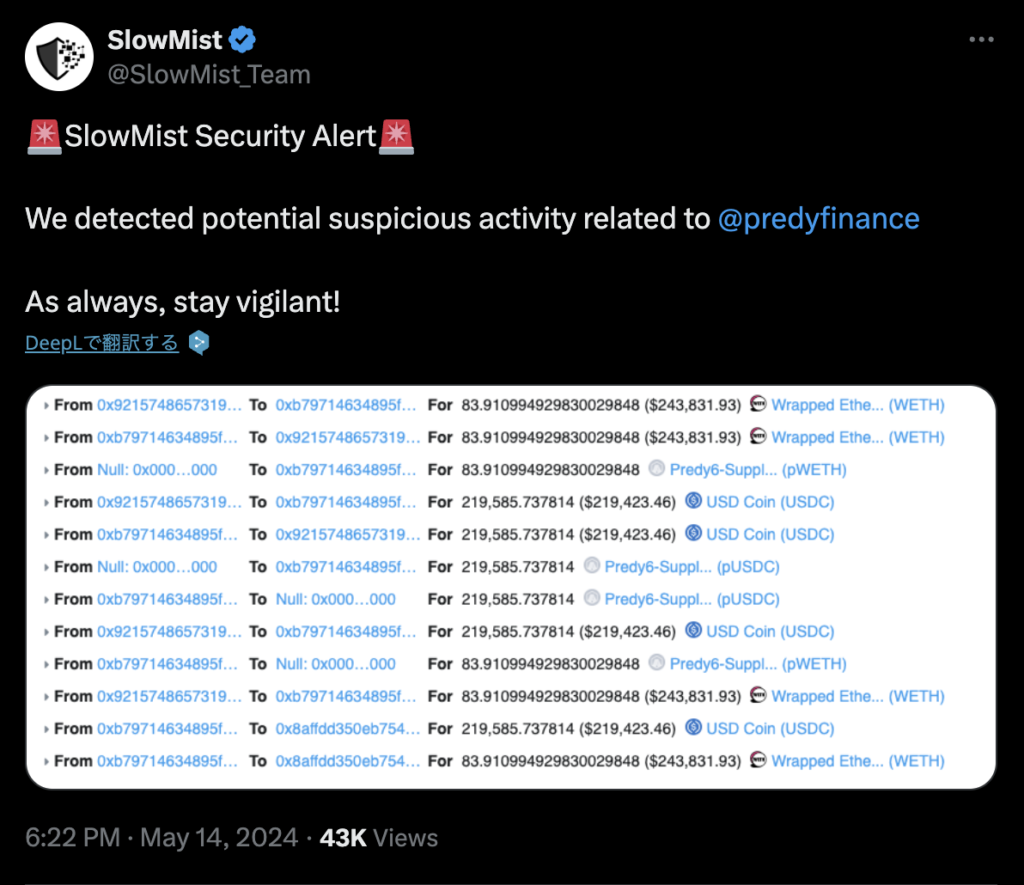
On May 14, 2024, the perpetual protocol “Predy Finance,” deployed on Arbitrum, suffered an exploit, resulting in approximately $460,000 being illicitly withdrawn from the pool funds. Predy Finance requested the return of the funds in exchange for a 10% bounty, but the perpetrator has not responded to negotiations, leading to a complete loss of the $460,000.
The fundamental cause of this incident, and openly sharing it, can serve as a valuable reference for other projects. When Bunzz requested an interview to discuss the issue, the Predy team responded promptly, offering an open and comprehensive explanation of the underlying causes, including their operational structure and development processes. With respect to the Predy team, who are already moving forward with development, we present the full details of the exploit.
What is Predy Finance? – Overview and Features
Predy is a DEX protocol offering intent-based perpetual futures and gamma short (leveraged Uniswap LP positions with delta neutrality). Deployed on the Arbitrum mainnet, it has steadily increased its total value locked (TVL). It features a unique lending pool mechanism, allowing up to 40x leverage in its perpetual protocol. The exploit targeted this lending pool mechanism.
Why Did the Exploit Occur?
The exploit was first detected not by the Predy team, but by SlowMist, a China-based Web3 cybersecurity company. “SlowMist likely flags contracts with a certain amount of pooled funds as potential incident sites,” said Ibe, a contributor from the Predy team. After being alerted by SlowMist’s post, the team quickly identified the cause.
HypernativeLabs, a platform providing risk prevention through on-chain data analysis, contacted Predy immediately and collaborated on troubleshooting.
“This was our first experience with an exploit as a team. Although we identified several necessary actions, having Hypernative Lab for external discussion and support was helpful,” said Ibe. The collaboration between previously unconnected projects and audit firms, based solely on on-chain analysis and social media posts, exemplifies the unique nature of Web3.
With HypernativeLabs’ advice, the Predy team rewrote access rights to the problematic contract functions, successfully eliminating the root cause. They officially announced on social media that the impact was limited to the lending pool, with no damage to customer assets, and detailed the exploit in a Medium post on May 16, 2024. While the protocol was not destroyed, Predy remains paused as of May 28, 2024, with efforts underway to resume operations.
Dissecting the Attack Method on Predy Finance’s contract
Predy Finance deployed the latest version, “V6,” on the Arbitrum mainnet in January 2024. The new V6 contracts, which had not undergone comprehensive auditing, became the target of the attack. Let’s explore how the attacker extracted $460,000.
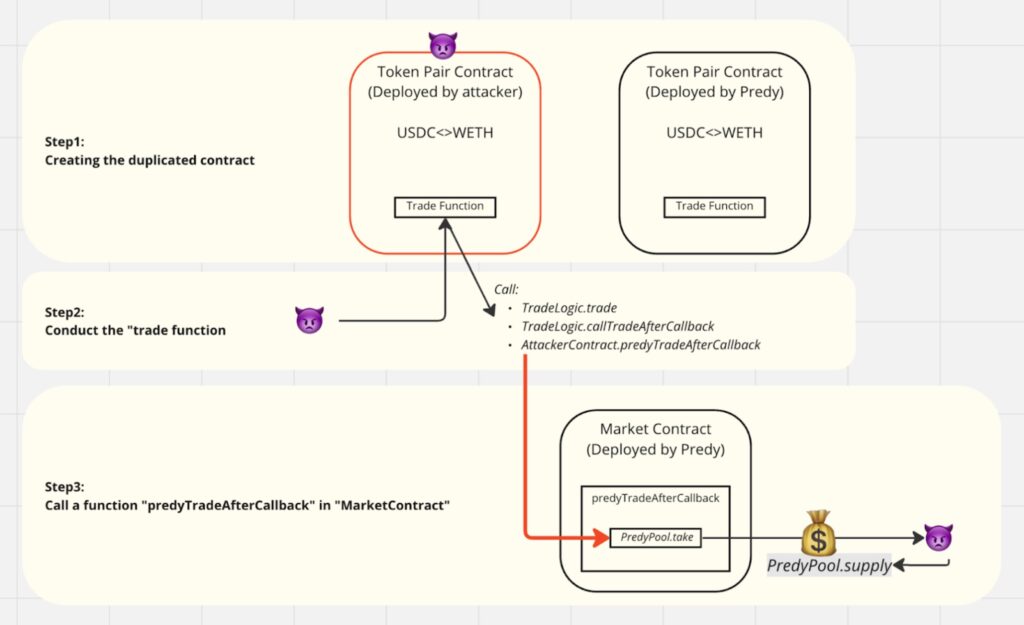
STEP 1: Creating Duplicate Smart Contracts
The attacker deployed contracts for token pairs targeted by the perpetual protocol. Predy allows users to create such contracts. The attacker deployed a contract identical to the existing USDC<>WETH contract.
STEP 2: Calling Functions in the Lending Pool Contract
The attacker, being the owner of the contract created in Step 1, called the “PredyPool.take” function of the lending pool contract. This was within the intended usage of Predy, allowing users to directly interact with contracts, including for flash loans.
STEP 3: Supplying to Self-Created Contracts and Moving All Funds
The attacker called the “PredyPool.supply” function, not to the appropriate protocol contract but to their self-created contract, moving all funds in two transactions.
Technical Root Cause of the Exploit
“Steps 1 and 2 were within expected usage. The issue arose in Step 3, where the supply destination was designated as the user’s contract,” said the Predy Team. While this attack method was simple, changing the supply destination, it raises the question of whether the vulnerability could have been detected earlier.
Operational Root Cause of the Exploit
“The incident occurred during a phase when we were achieving PMF and our overall team capabilities were being tested, but before our framework was fully established,” the Predy team explained.
Predy had conducted multiple major updates up to V6, releasing versions up to V5 as MVPs to test market acceptance and revenue models without significant audit costs (only acquiring two audit reports previously and using ImmuneFi for bug bounties).
Such dilemmas often arise for projects before funding. Comprehensive audits from top-tier firms are essential but can cost tens to hundreds of thousands of US dollars, which is seen as excessive for pre-PMF products. This is a realistic view of the risks and security measures for pre-PMF projects.
The Predy team candidly shared that previous audit reports from well-known firms were costly but lacked substance, merely serving as a “stamp of approval.” They doubted that even those firms would have identified the current vulnerability. This highlights the variability in audit report quality, which remains an industry challenge. Sometimes audit reports are demanded by CEXs or investors as part of due diligence, prioritizing the “stamp” over identifying vulnerabilities, thus lowering average audit quality.
This industry challenge is one reason Bunzz started its audit services. We empathize with Ibe’s perspective and believe that the industry’s lack of low-cost, high-quality audit services is problematic. Bunzz Audit leverages AI and a vulnerability database to reduce costs and move away from manual audits. Numerous early-stage products have already utilized our services. We are also considering performance-based business models, so interested projects are welcome to consult us.
The Future of Predy Finance
“The exploit targeted the pool contract’s vulnerability, not a critical security flaw in the perpetual protocol. Predy aims to scale with its intent-based architecture while paying more attention to overall contract vulnerabilities. Reflecting on the exploit, we started a $100,000 bug bounty on Code4rena. No user assets were stolen; only project assets were affected, making it a valuable experience. We achieved PMF with V6 and feel confident in our ability to scale,” said Ibe.
He added, “The exploit highlighted issues in our development process. Frequent contract updates post-audit necessitated repeated audits, which were impractical due to cost and schedule. We plan to incorporate quick vulnerability scanning tools into our development process.”
Bunzz Audit to Begin Continuous Auditing for Predy
As mentioned, Bunzz Audit has started trialing performance-based audit services. Inspired by our interview, we offered to audit Predy for free, which they gladly accepted. We plan to apply advanced approaches like Formal Verification, Fuzzing, and Dynamic Analysis, challenging for human audits, to Predy’s contracts.
- Fuzzing: A testing method that inputs large amounts of random or semi-random data to a program to observe its behavior.
- Formal Verification: A mathematical approach to proving that software or systems meet specified characteristics.
- Dynamic Analysis: A method of running programs and monitoring their runtime behavior to detect bugs or security issues.


